Think Like a Hacker, Secure Like a Fortress.
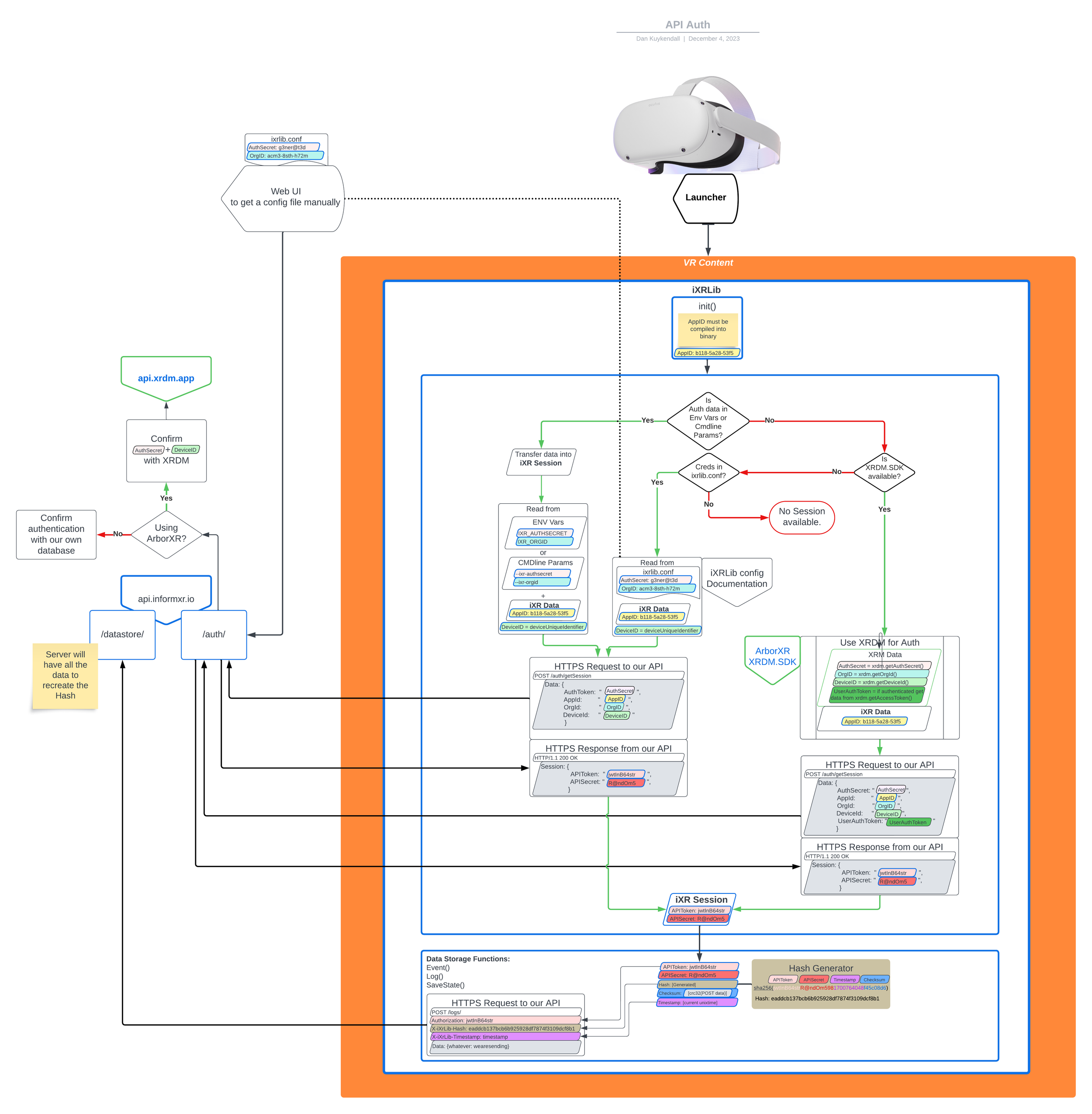
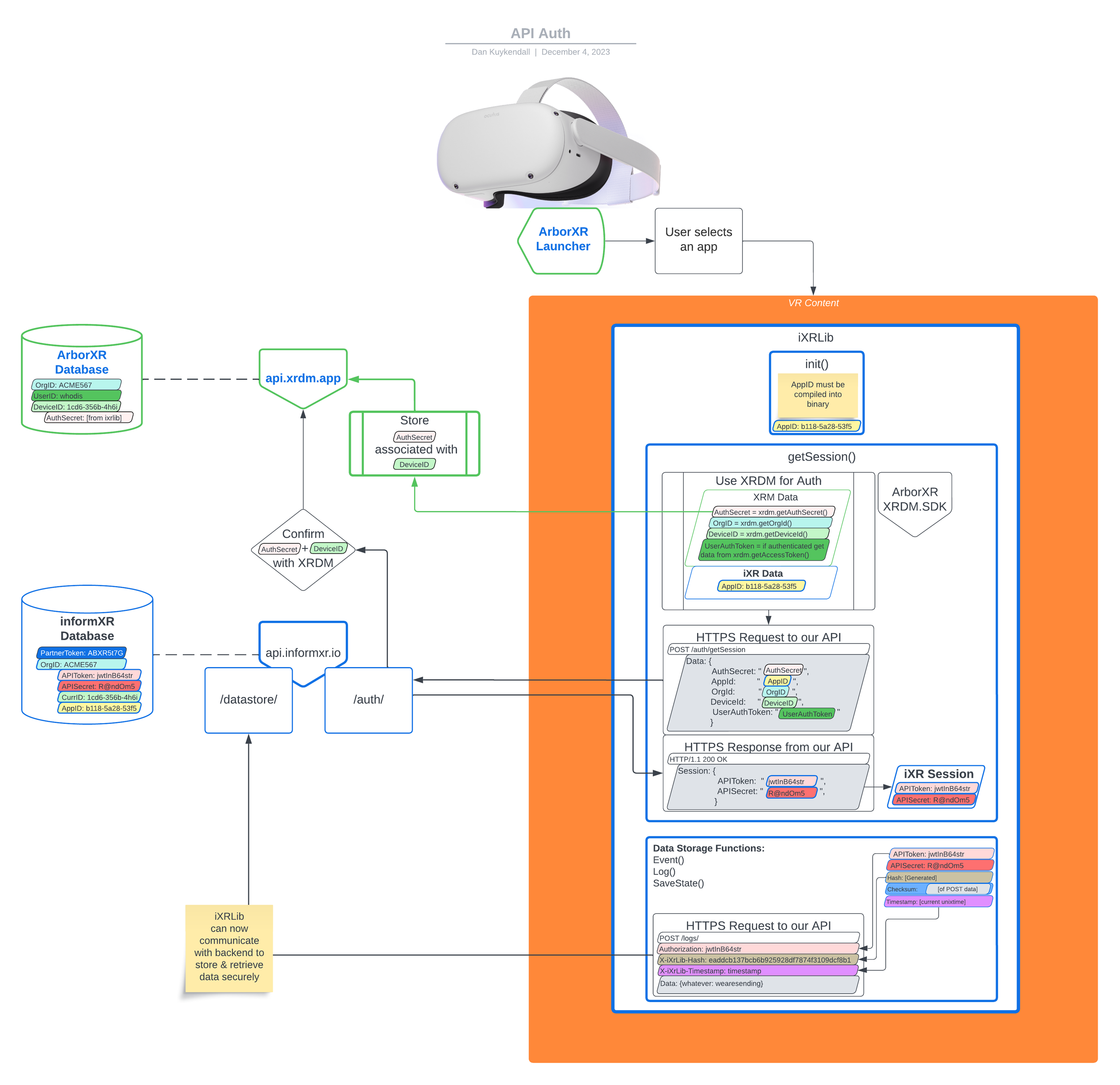
Authentication workflow
We prioritize security through transparency, ensuring our developers are fully informed about our robust authentication models. This vital information not only proudly showcases the security your data is put under, but also will shape the way you interact with and integrate our technology into your systems.